Data Integrity
Data Integrity
- Data stored on a computer should always be accurate, consistent and up to date.
- Two of the methods used to ensure data integrity are validation and verification.
- The accuracy (integrity) of data can be compromised
- during the data entry and data transmission stages
- by malicious attacks on the data, for example caused by malware and hacking
- by accidental data loss caused through hardware issues
Data integrity
Two of the methods used to ensure are validation and verification
Validation
Validation is a method of checking if entered data is reasonable (and within a given criteria), but it cannot check if data is correct or accurate.
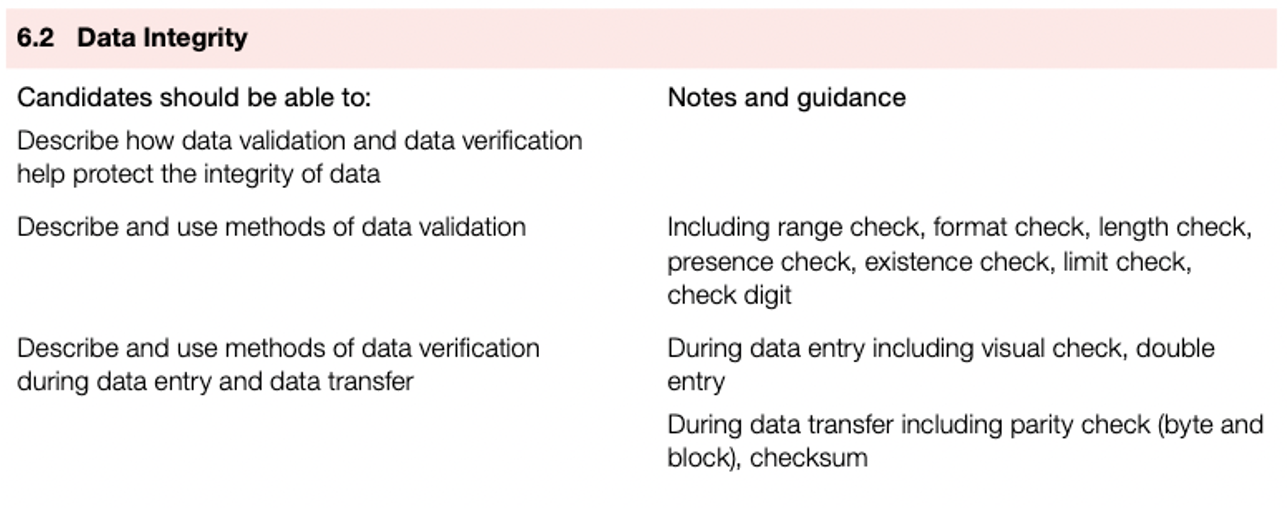
Validation methods:
- type check
- range check
- format check
- length check
- presence check
- existence check
- limit check
- consistency check
- uniqueness check
Check digits
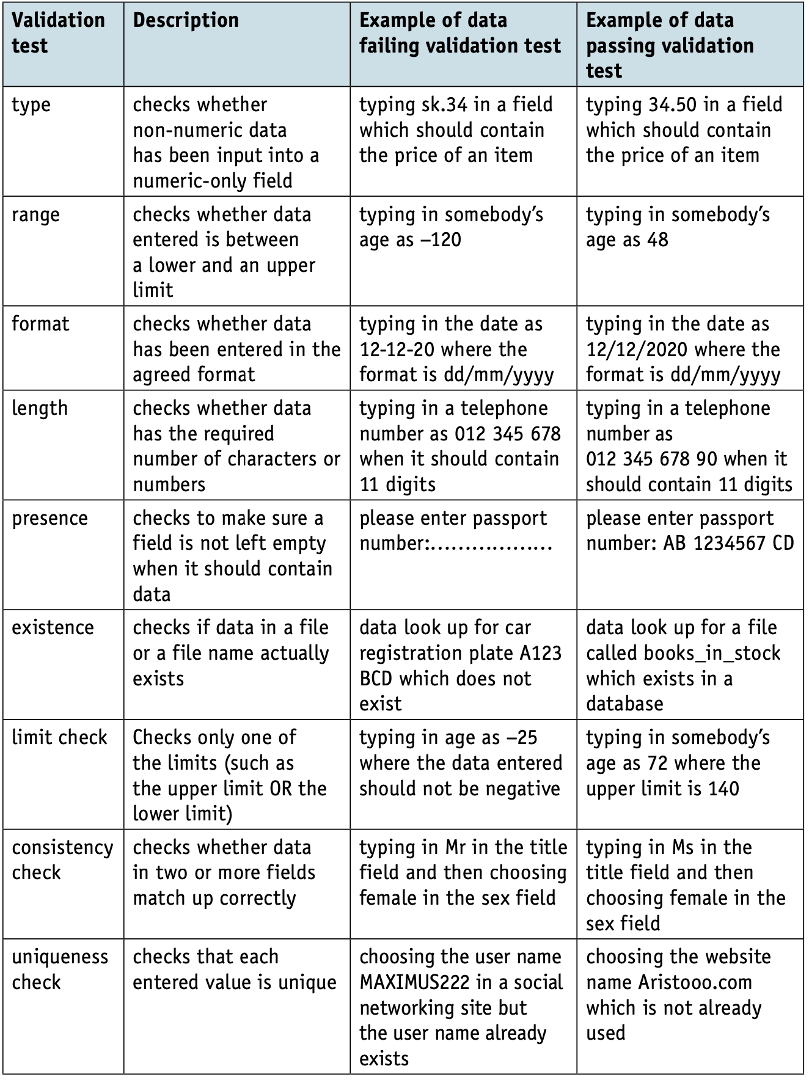
- The check digit is an additional digit added to a number.
Check digit
- The check digit is an additional digit added to a number.
- An example of a check digit calculation is modulo-11.
- The following algorithm is used to generate the check digit for a number with seven digits.
Data integrity
is a method of checking if entered data is reasonable (and within a given criteria), but it cannot check if data is correct or accurate
Data integrity
Which method checks whether data entered is between a lower and an upper limit
Data integrity
Which method checks whether data has the required number of characters or numbers
Data integrity
Which method checks to make sure a field is not left empty when it should contain data
Verification
- Verification is a way of preventing errors when data is entered manually (using a keyboard, for example) or when data is transferred from one computer to another.
Double entry
- Data is entered twice, using two different people, and then compared.
Visual check
- Entered data is compared with the original document.
Verification during data transfer
- When data is transferred electronically from one device to another, there is always the possibility of data corruption or even data loss.
- A number of ways exist to minimise this risk.
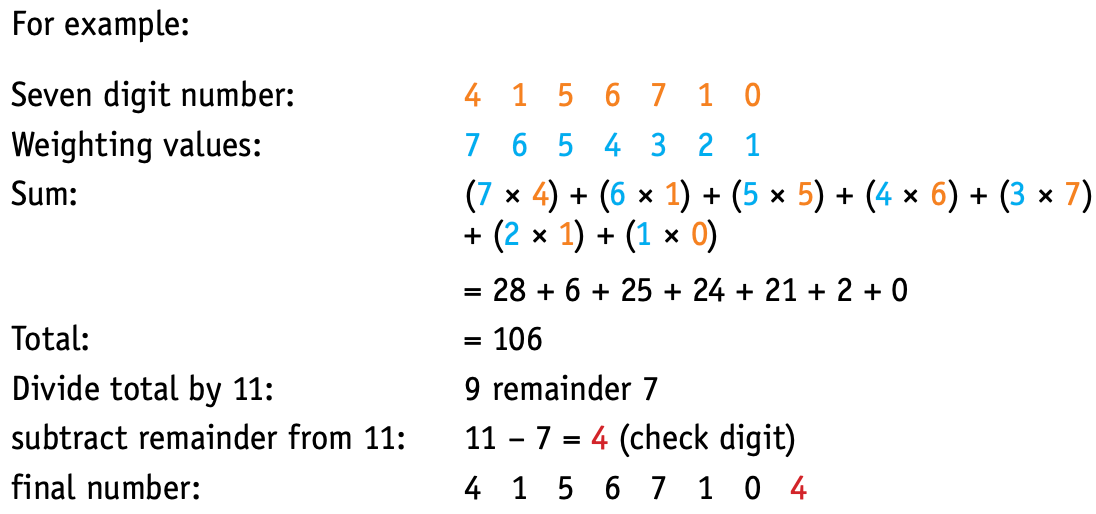
Checksums
- A checksum is a method to check if data has been changed or corrupted following data transmission.
- Data is sent in blocks and an additional value, the checksum, is sent at the end of the block of data.
Parity check
- A parity check is another method to check whether data has been changed or corrupted following transmission from one device or medium to another.
- A byte of data, for example, is allocated a parity bit. This is allocated before transmission.
- Systems that use even parity have an even number of 1-bits; systems that use odd parity have an odd number of 1-bits.
- Naturally, any of the bits in the above example could have been changed leading to a transmission error.
- Therefore, even though an error has been flagged, it is impossible to know exactly which bit is in error.

- Parity blocks is a block of data is sent and the number of 1-bits are totalled horizontally and vertically.
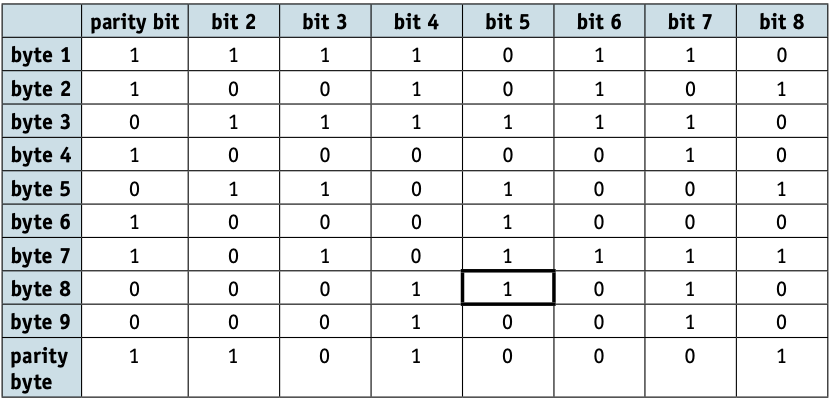
- A careful study of the table shows that
- byte 8 (row 8) has incorrect parity (there are three 1-bits)
- bit 5 (column 5) also has incorrect parity (there are five 1-bits).
Automatic repeat request (ARQ)
Automatic repeat request (ARQ) is another method to check data following data transmission.
- ARQ uses acknowledgement (a message sent to the receiver indicating that data has been received correctly) and timeout (the time interval allowed to elapse before an acknowledgement is received).
- When the receiving device detects an error following data transmission, it asks for the data packet to be resent.
- If no error is detected, a positive acknowledgement is sent to the sender.
- The sending device will re-send the data package if it receives a request to re-send the data, or a timeout has occurred.
- The whole process is continuous until the data packet received is correct or until the ARQ time limit (timeout) is reached.
Data integrity
is a way of preventing errors when data is entered manually (using a keyboard, for example) or when data is transferred from one computer to another
Data integrity
Verification normally includes:
Data integrity
Data is sent in blocks and an additional value, the , is sent at the end of the block of data.
Data integrity
A refers to an error detection method where an extra bit, or a parity bit, is added to each data unit
Data integrity
(ARQ) is another method to check data following data transmission.
Data integrity
Find the parity bits for each of the following bytes:
1101101 even parity used
1110100 odd parity used
Data integrity
ARQ uses (a message sent to the receiver indicating that data has been received correctly) and (the time interval allowed to elapse before an acknowledgement is received).